Defending and Attacking Embedded Systems: Modern Cybersecurity in IoT Devices

Slide-1
Defending and Attacking Embedded Systems
Modern Cybersecurity in IoT Devices: Cryptography & Computer Engineering/Sciences
REU Scholars: Isaac Merlin & Emily Wayne
Mentor: Dr. Reza Azarderakhsh
Research Assistants: Aimee Laclaustra, Rabih El Khatib, Daniel Owens

Slide-2
Objective
- Classic Cryptography shift to Post Quantum Cryptography (PQC)
- Modern implementations of cryptography
- National Institute of Science and Technology (NIST) standardized post-quantum algorithm, KYBER.
- Embedded systems; Hardware and Software Implementations
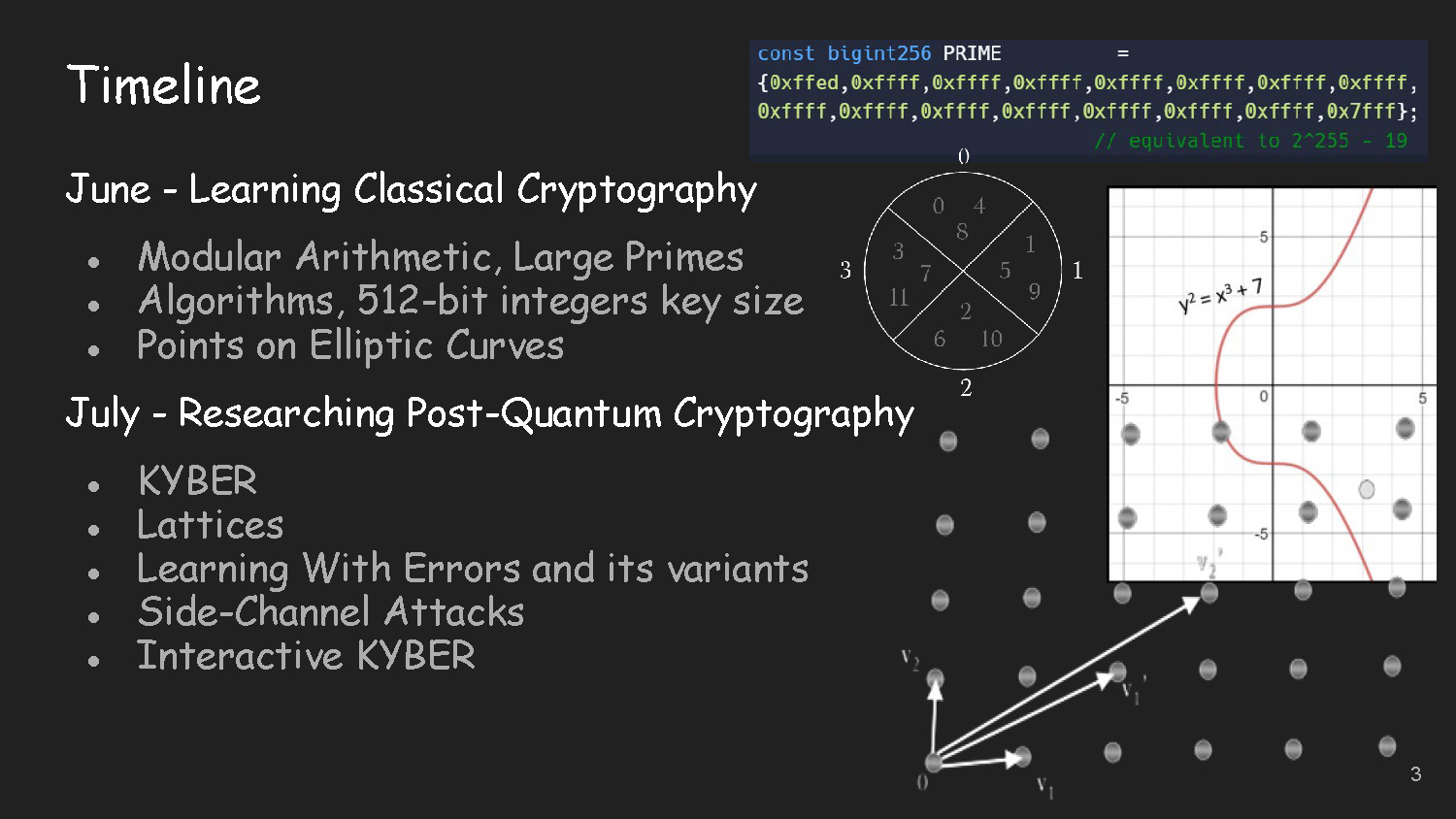
Slide-3
- Modular Arithmetic, Large Primes
- Algorithms, 512-bit integers key size
- Points on Elliptic Curves
July - Researching Post-Quantum Cryptography
- KYBER
- Lattices
- Learning With Errors and its variants
- Side-Channel Attacks
- Interactive KYBER
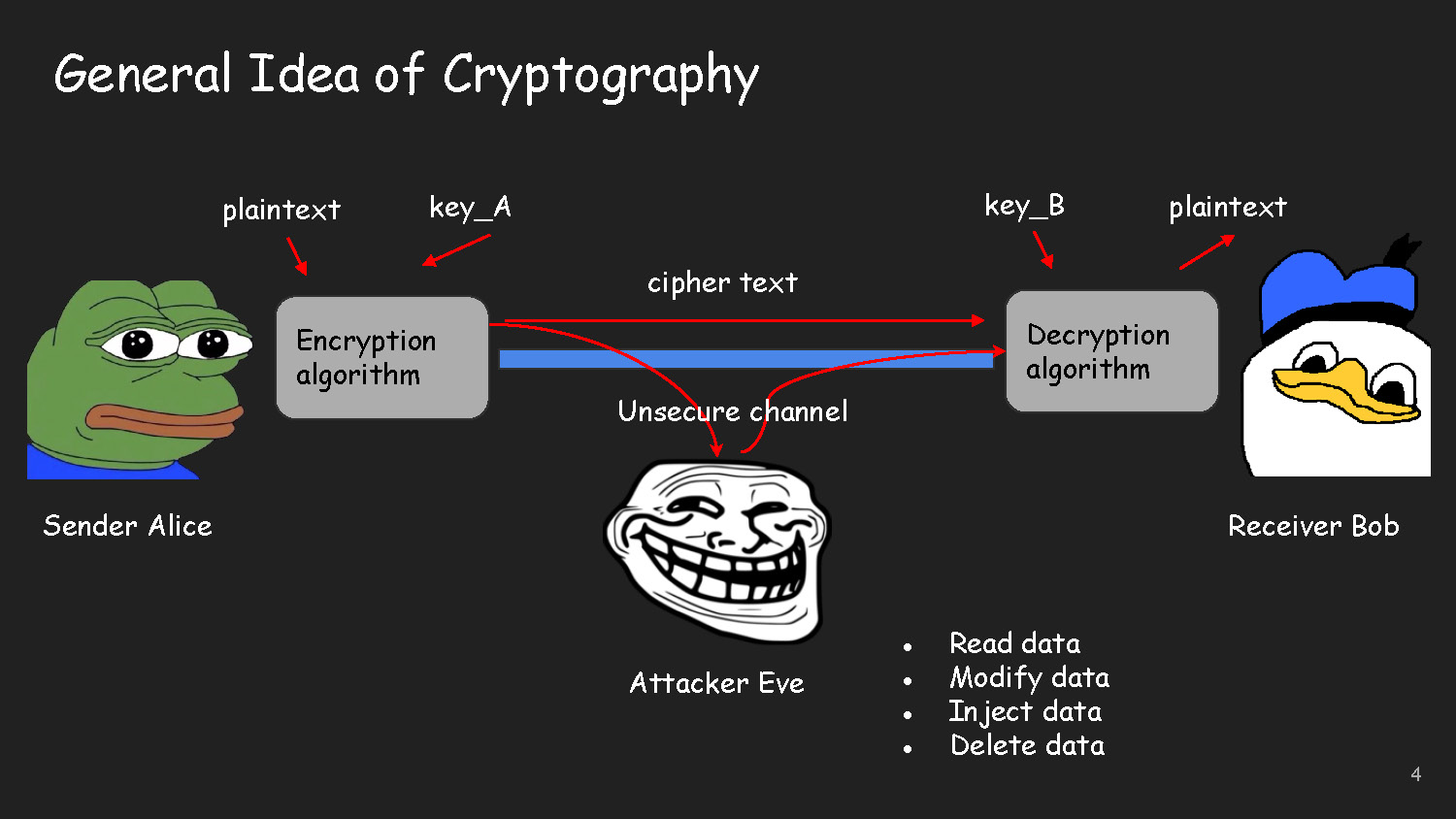
Slide-4
General Idea of Cryptography
The diagram shows the communication flow between Sender Alice and Receiver Bob through an unsecure channel. Alice uses an encryption algorithm with key_A to convert plaintext to cipher text. Bob uses a decryption algorithm with key_B to convert the cipher text back to plaintext. An Attacker Eve can potentially:
- Read data
- Modify data
- Inject data
- Delete data
The diagram illustrates the flow from plaintext through encryption algorithm to ciphertext across an unsecure channel, then through decryption algorithm back to plaintext.
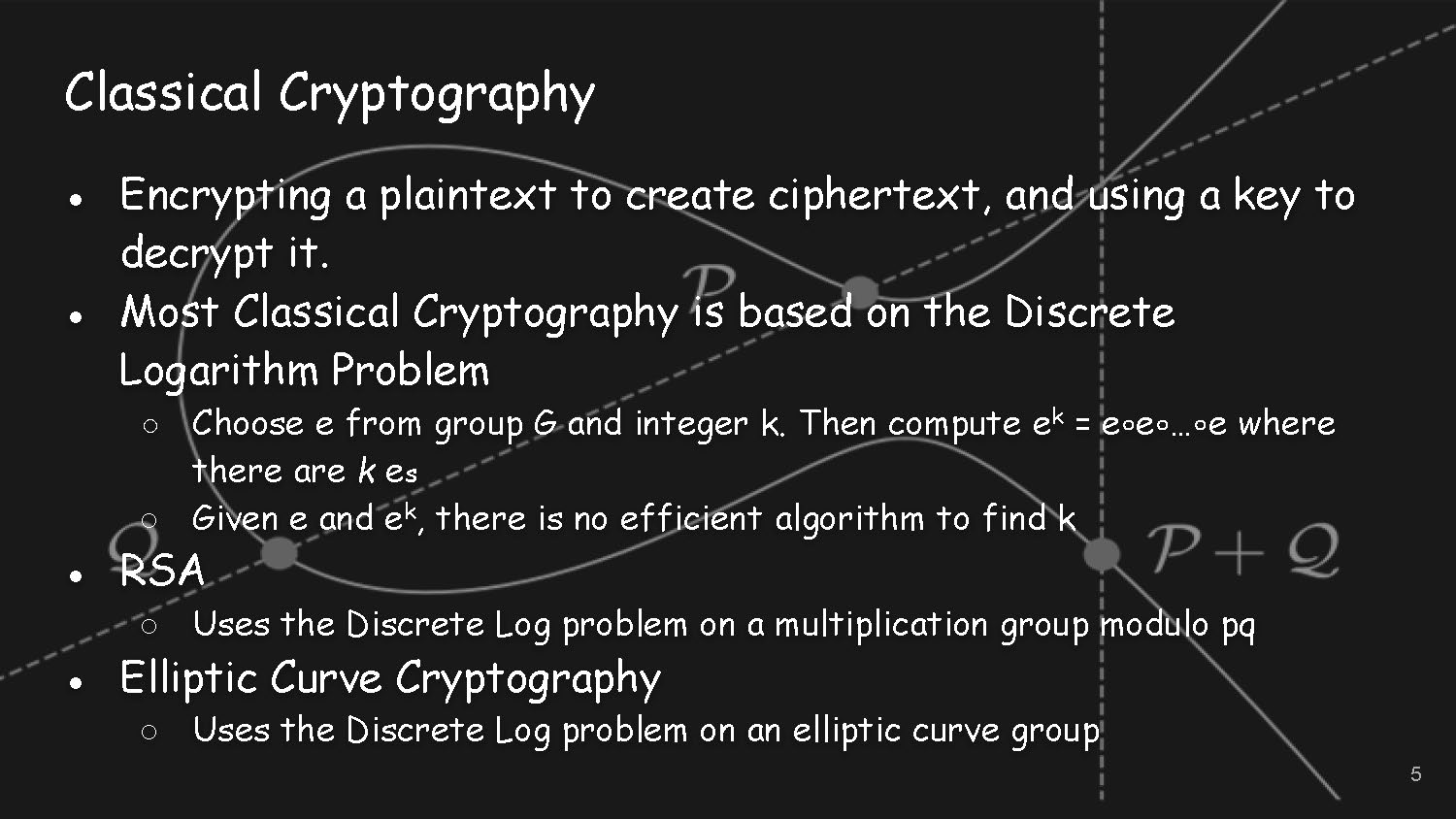
Slide-5
Classical Cryptography
- Encrypting a plaintext to create ciphertext, and using a key to decrypt it.
- Most Classical Cryptography is based on the Discrete Logarithm Problem
- Choose e from group G and integer k. Then compute ek = e∘e∘…∘e where there are k e s
- Given e and ek, there is no efficient algorithm to find k
- RSA
- Uses the Discrete Log problem on a multiplication group modulo pq
- Elliptic Curve Cryptography
- Uses the Discrete Log problem on an elliptic curve group
Slide-6
Attack : Shor's Algorithm
On a classical computer, it takes subexponential time to break algorithms like RSA, using the general number field sieve.
General number field sieve : O(e^((64/9)1/3•log(n)1/3•log(log(n))2/3)) to factor n
But on a quantum computer, any discrete logarithm based cryptographic scheme can be broken in polylogarithmic time, using shor's algorithm.
Shor's Algorithm: O(log(n)2•log(log(n))•log(log(log(n)))) to factor n
This difference is huge, it is the difference between computing for millenia and seconds.
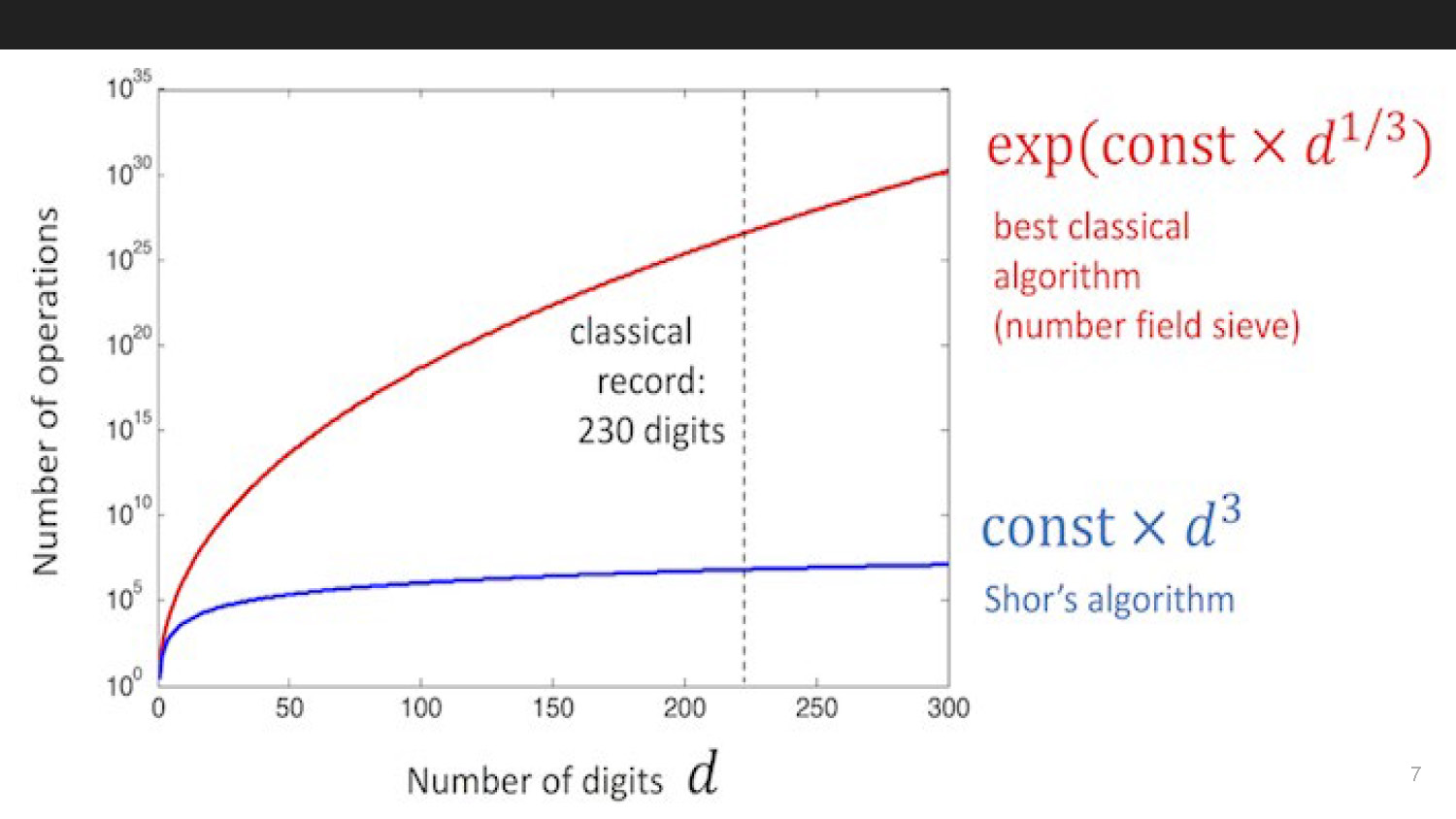
Slide-7
This slide contains a visual representation comparing classical and quantum computing approaches to cryptographic attacks, illustrating the dramatic difference in computation time.

Slide-8
Post-Quantum Cryptography - NIST Standards
- According to National Institute of Science and Technology, they identified algorithms to be standardized including CRYSTALS-KYBER
- Need to learn about contemporary cryptographic algorithms that protect data and communications
- Current standards
- General Encryption: CRYSTALS-Kyber
- Digital Signatures: CRYSTALS-Dilithium
- These are both based on Lattices, and more specifically LWE.
do it
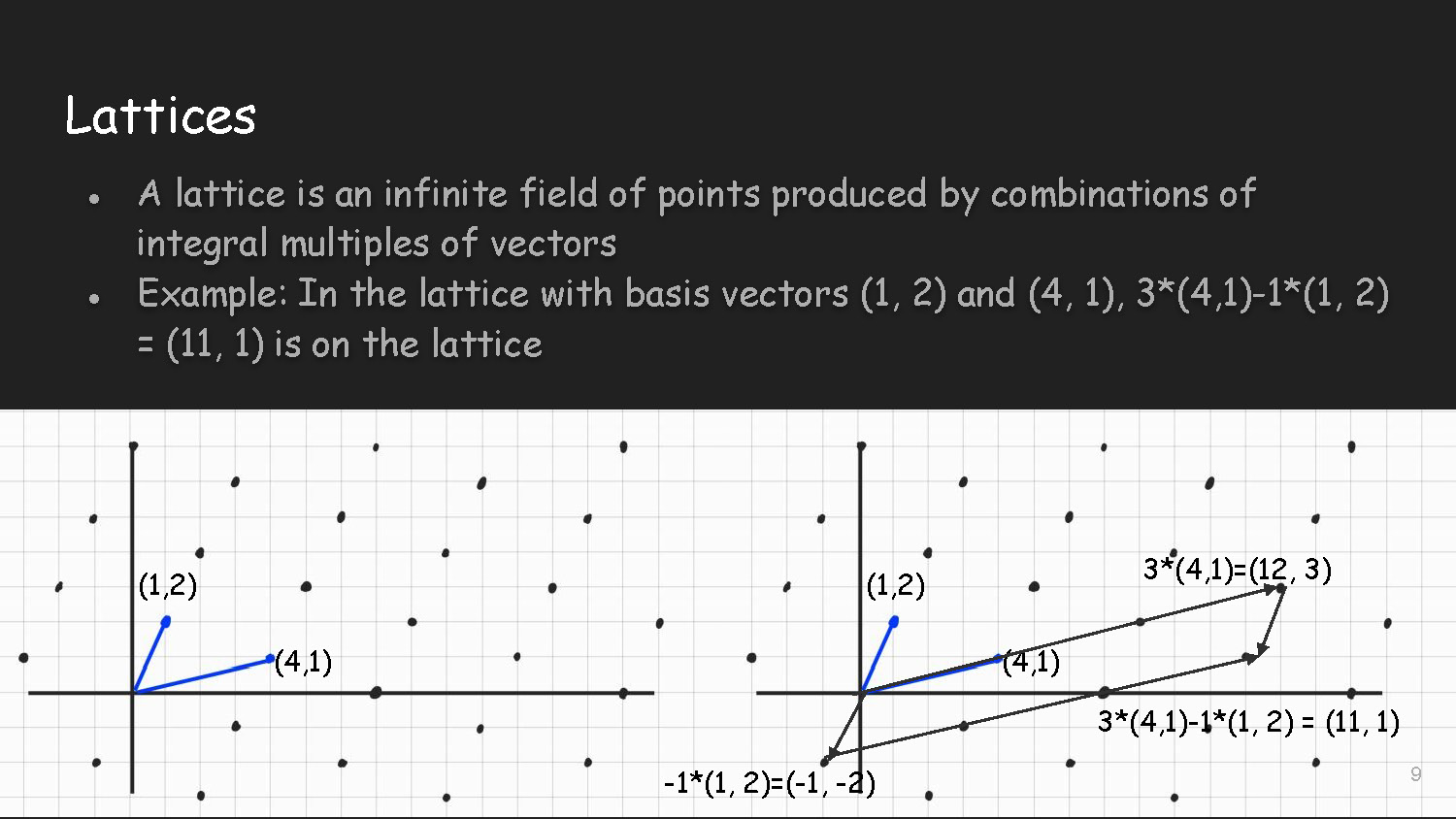
Slide-9
Lattices
- A lattice is an infinite field of points produced by combinations of integral multiples of vectors
- Example: In the lattice with basis vectors (1, 2) and (4, 1), 3*(4,1)-1*(1, 2) = (11, 1) is on the lattice
The diagram shows basis vectors (1,2) and (4,1) on a coordinate grid. It illustrates the calculation: 3*(4,1)=(12, 3), -1*(1, 2)=(-1, -2), and the result 3*(4,1)-1*(1, 2) = (11, 1)
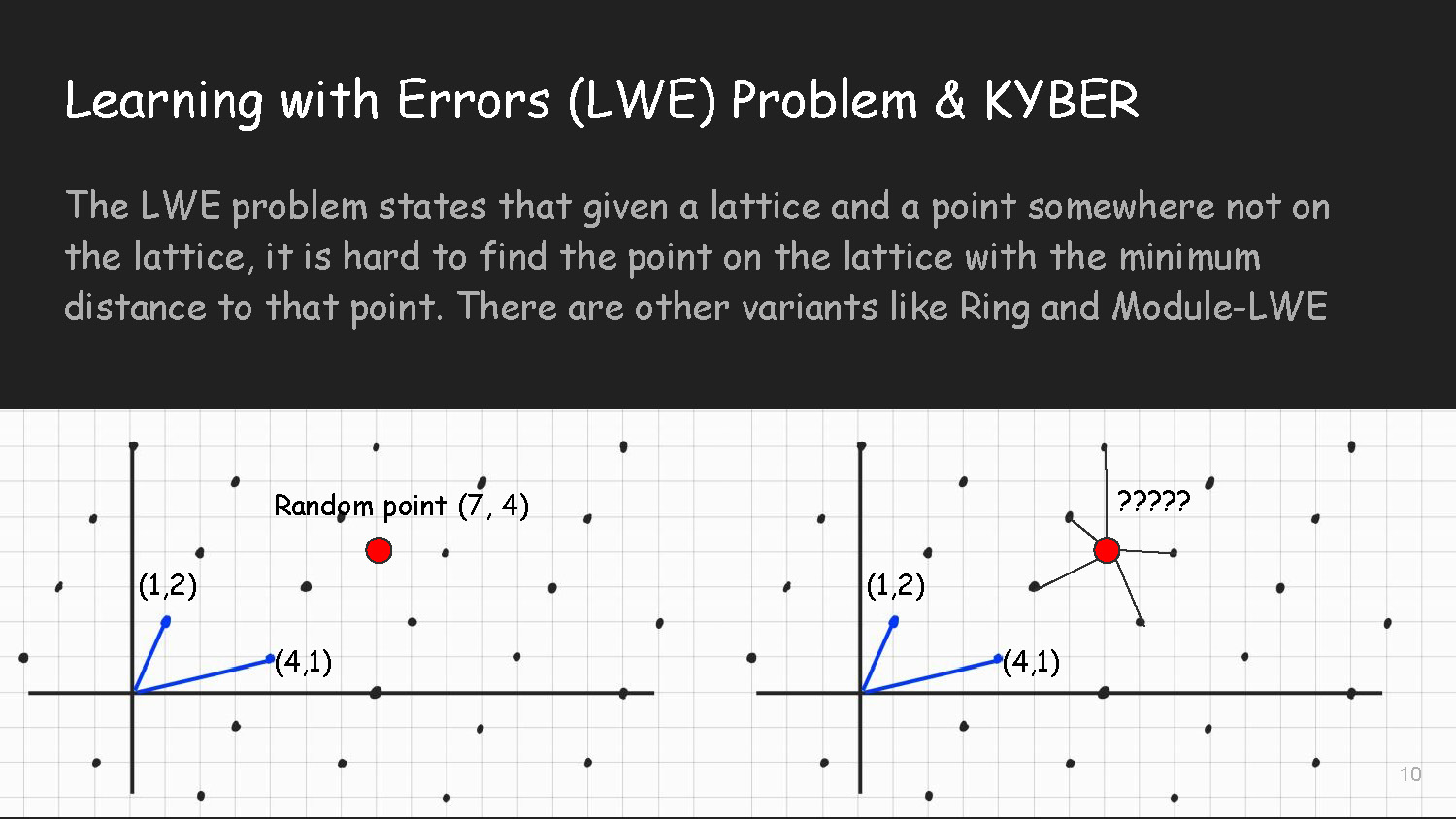
Slide-10
The LWE problem states that given a lattice and a point somewhere not on the lattice, it is hard to find the point on the lattice with the minimum distance to that point. There are other variants like Ring and Module-LWE
The diagram shows basis vectors (1,2) and (4,1) with a random point (7, 4) not on the lattice. Question marks indicate the challenge of finding the closest lattice point to the random point.
Slide-11
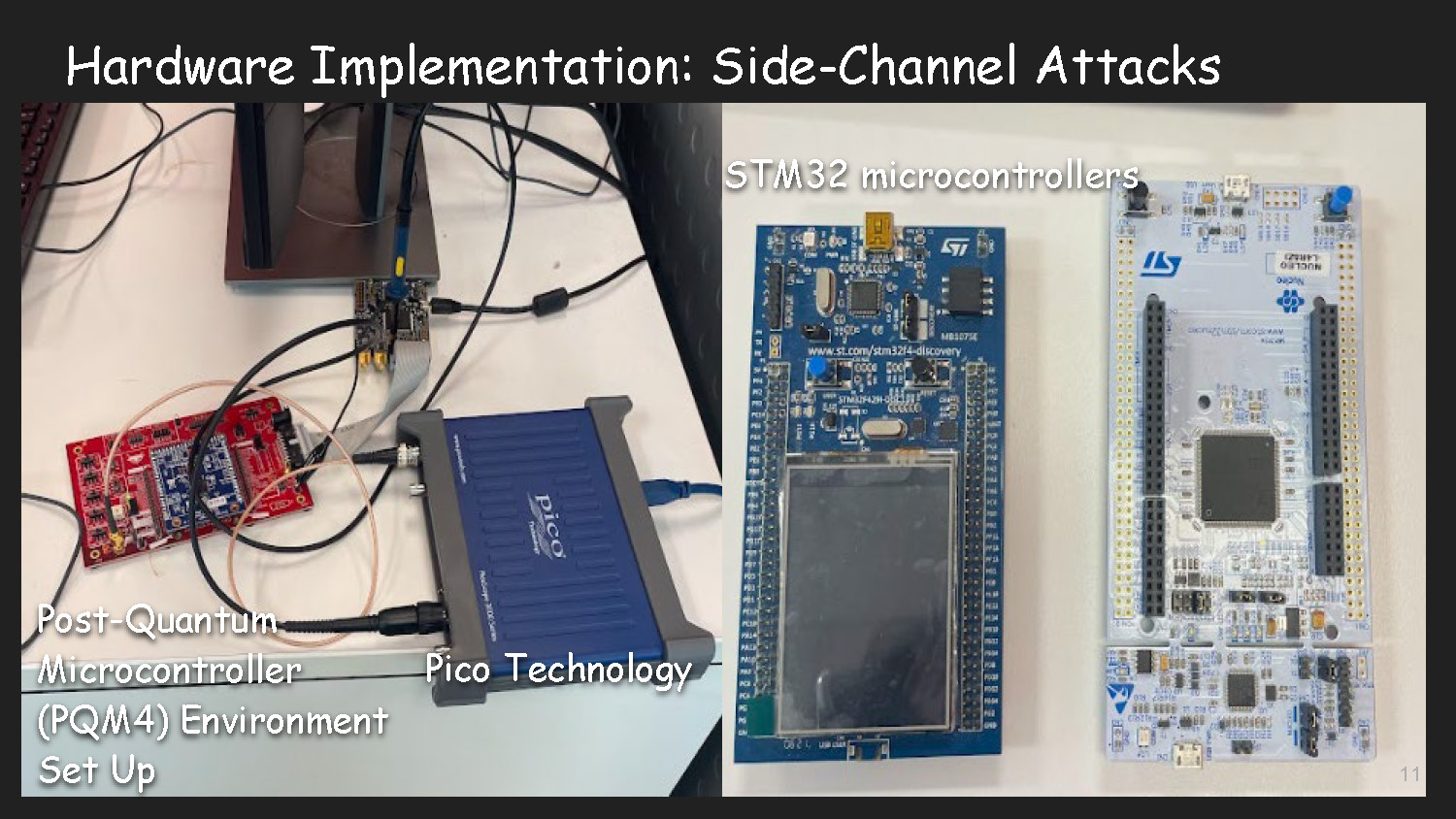
Hardware Implementation: Side-Channel Attacks
STM32 microcontrollers
Pico Technology
Post-Quantum Microcontroller (PQM4) Environment Set Up
The image shows hardware components including microcontroller boards and measurement equipment used for side-channel attack research.

Slide-12
Conclusion
- Classical cryptography may no longer be secure with computational advancements in computers
- Newer implementations including KYBER involve the study of lattices and Learning With Errors (and its variants)
- It is important to continue to be secure from side-channel attacks when updating to new quantum-resistant cryptographic algorithms
- Improvements: make cryptography more interactive for younger audience to understand importance of data and communications

Slide-13
thank

End of Presentation
Click the right arrow to return to the beginning of the slide show.
For a downloadable version of this presentation, email: I-SENSE@FAU.